

Authentication factors are additional information that must be presented by an user after he provides his email and password in order to complete the login proccess.
The following factors are supported:
Authentication factors are disabled by default when you create an application, but it's really easy to enable them by navigating to the Application Settings page and choosing the Authentication Factors tab:
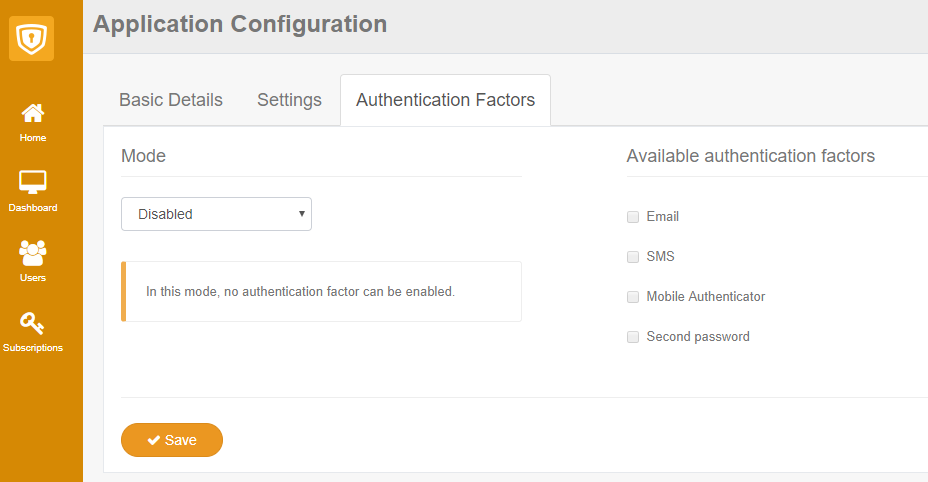
There are two modes available when enabling the factors:
You may want to add security to specific actions or operations in your application by requesting that one or multiple factors are presented by the user.
In order to accomplish this, GrantID (HML) provides a special JWT token named Auth Token whose content is shown below:
{
"nbf": 1500940579,
"exp": 1500940879,
"iss": "http://sub.grantid.com",
"auth_factor": [
"email",
"mobile_app"
],
"sub": "ed6adcde-2e5e-488b-8afb-eecf33bec202"
}
This token is issued after an user successfully completes a number of authentication factor requests. It has a default expiration of 5 minutes and contains the following information:
To retrieve an Auth Token for an user, an Application must redirect the user (preferably already authenticated) to the GrantID (HML) /Factor/Authenticate URI and provide the following parameters:
Additional query parameters in the return URL do not need to be registered, as you may have a single callback that redirects to multiple pages inside
your application.
For instance, if you want the user to be redirected to https://app.com/Auth/Callback?r=/Home/Restricted you may register only
https://app.com/Auth/Callback in the Application Settings page.
| Authentication Factor | Key |
|---|---|
| SMS | sms |
| Mobile Authenticator | mobile_app |
| Second Password | second_password |
The following example requests both the Email and Mobile Authenticator factors:
GET /Factor/Authenticate?redirectUrl=http%3A%2F%2Fapp.com%2FHome%2FAuthCallback%3Fr%3D%2FHome%2FRestricted&clientId=app&factors=email%20mobile_app Host: sub.grantid.com
The redirect to GrantID (HML) must come from an URL that is registered to an application or else the request will fail.
Do not forget to URL encode the parameters or else the request will also fail.
After the user successfully completes the factors request, he will be redirected to the requested URL which will have an additional parameter named "auth_token" whose value is the Auth Token.
Finally, it's the responsibility of the application to validate the following information inside the token:
Even though the token has a fixed expiration of 5 minutes, you may use the nbf and exp parameters to determine a smaller window of validity per operation/action of your application.